1. Wireless Ethernet & CD driver program
2. Access Point & Router configuration CD
3. Channel internet connection
4. NOS
C. BASIC THEORY
Wireless Local Area Network (WLAN)
Maybe for some people this term is not foreign even more impressed already stale. However, few of them do not forget or not even know what it is to WLAN. WLAN is actually a local network (LAN) that uses the media intermediaries high frequency radio signals, not using the cable. Wireless LAN has a level of flexibility that is higher than the cable media. Therefore, a WLAN is often used as an extension of the communication cable through the media or as an alternative media for communication through the cable.
WLAN technology to allow users to build a wireless network in an area that is local (for example, in the office building environment, building on the campus or public area, such as airport or cafe). WLAN can be used in temporary offices or where permanent installation cable is not allowed. WLAN, or sometimes built as a supplement to the existing LAN, so users can work on many different locations within the building. WLAN can be operated in two ways. In infrastructure WLAN, the wireless station (peranti with a radio network card or external modem) to connect to a wireless access point that serves as a bridge between the station-station and the network backbone that is at that time. In a WLAN environment is a peer-to-peer (ad hoc), some users in limited areas, such as meeting rooms, can form a temporary network without using the access point, if they do not need access to network resources.
Network Wireless Ad-Hoc
Wireless networks using the 802.11 standard, has a feature that allows the client in each other can communicate with each other with the method of peer-to-peer directly through their wireless devices. Features that one is often called the term Ad-Hoc. In Ad-Hoc topology this, each laptop, PDA, or other wireless device berkemampuan can act as a node is independent and form a network itself, irrespective of what has been provided by the AP in its vicinity. You can imagine, the wireless network Ad-Hoc akan This can make trouble for the actual wireless network. Form a network with its own outside of the wireless network from the AP that there is, of course there are some issues that will ditimbulkannya. First, the Ad-Hoc network may be using the limited frequency bandwidth that is also used by wireless networks indeed. So, between Ad-Hoc network with the wireless network must surely share the frequency bandwidth. Of this enough of the wireless network that actually.
Another problem that can be embossed with the Ad-Hoc network is a network security which is the main open. Network Ad-Hoc wireless this can be a gateway for intruders to enter into the main network. This is because the network is very difficult to centrally regulated. The radio signal monitoring propagasi also almost impossible. Ad-Hoc network becomes easier to be penetrated and dikacaukan because memonitornya this difficulty. Moreover the hacker can easily enter into the main network in a way to make a hacking device that is incorporated in the Ad-Hoc network and then perform bridging to the main network. The road to the main network to be wide open.
One needs to do is make the Ad Hoc network. Ad Hoc network is a network that only connects to the computer via the computer without a hub or router as access point. For wireless home network or small office network is using this type. Therefore, the one that should not be missed is to provide a check on the option This is a computer-to-computer (ad-hoc) network, wireless access points are not used. This option is located on the bottom screen Association. When done press OK.
What purpose of the term 802.11a/b/g?
802.11a/b/g term is a standardized number of WLAN systems that have at this time. Standardization in this set what and how to work a WLAN network. Starting from the signal modulation techniques, the frequency of its range, until a suitable type of antenna used. Each standard has a technical specification that is different. Thus I work, the device support, and the resulting performance of each standard is different from one another.
As a result of this situation, the three standards can not be related to one another. That is the device that use the 802.11a standard will not be able to work on the AP using the 802.11b standard, so further.
Perhaps the most user wireless networks certainly have heard the term that consists of numbers and letters this. It is true that when you want to use the wireless network, it must first know the device works in which the standard. Because if you buy a device that does not fit with AP or other wireless device, you may not be connected to the network. Therefore, it is recommended examining first wireless device to work on what type.
Currently, the most common standard used is standard 802.11b and 802.11g. However, it was not uncommon at this time also a wireless device is deliberately made with the ability to work in the third standard. So a device equipped with three different specifications. Thus, it is not difficult to be connected.
Type the security of wireless networks is as follows:
1. WPA (Wifi Protected Access), WPA established techniques to provide encryption of data that point to be weak WEP, and provides user authentication is lost on the development of the concept of WEP
2. IP Address restrictions with subnetting
3. Using WEP (Wireless Encryption Protocol) and most of the product is obtained from the access point may be to buy a WEP vulnerable to it but there is minimal protection during the early use 128-bit WEP, while 802.11a uses 152-bit WEP encryption
4. Change the SSID (Service Set ID) the default access point or wireless router that is used. Similarity SSID enyebabkan many users are in the scope of the software AP (Access Point) hackers or other wireless networks
5. Implementation of a closed network mode where all users have wireless network or directly connected to the intermediary Tapa AP or wireless router power off mode "Ad-Hoc" connection that allows peer-to-peer network between the wireless card
6. MAC Address Authentication in addition to the insert in the ACL (Access Control List) configuration access point that used to only accept connection requests from users with specific MAC Address, or by limiting the amount
7. Turn off the mode: Broadcast, "which allows the access point SSID periodic use its
8. Run the SNMP (Simple Network Management Protocol) on the access point. Setting the network name with the name that is not common.
9. With periodic audits conducted melaukan scanning access point in the area around the wireless network
10. In place on the access point subnet and use a firewall between the subnet with a subnet or network on top of
11. Virtual Private Networking (VPN) in a wireless network that is used, the Virtual Private Network is a system that allows of a private network on the public infrastructure.
D. ENGAMBILAN DATA
The steps:
1. the wireless radio (green image, called SMC wireless)
2. Practice wireless static
ü Make IP settings in the Wireless Adapter's Control Panel
ü In the radio do configuration, and then give the name of the SSID
SSID: goleklayangan
ü Then determine which channel will be used
Select mose Adhoc connection with
ü Apply config
ü Conducting site surveys and double click on the SSID that will be
ü Ping IP through a computer
Example: click Start → Run → type in: \ \ 192.168.5.4 (the IP through)
3. Wireless dynamic practice
ü Set the IP to dynamic [dhcp]
ü Perform site survey and click 2 times on the SSID will be
ü Ping IP through a computer
E. ANALISA
Before praktikan analyze results praktikum, praktikan akan first explain how to install, configure, and setting up the wireless LAN network. Here is how to work pngkonfigurasian and penyetingannya.
First, there are 2 ways penyetingan, namely:
1. Setting up wireless static, as follows:
If there is a local area connection, then disable the telebih before WLAN configuration is done.
1. Setting up IP address on the host is as follows:
a. select my network places right Klick properties
b. select local area conection right Klick select properties
c. select the general tab, then select the conection using protocol TCP / IP properties select
d. fill in the IP address in accordance with the network address (192.168.5.4 is here
e. then select the option on the DNS server using preference, the preferred DNS server IP address fill in accordance with the IP Address Server, here is the address 192.168.5.4
f. OK then, the IP address setting is completed.
2. Check process control, until the perfect wireless device recognized by the operating system such as picture 1, with the steps:
Desktop right click My Computer Properties Hardware Tab Device Manager the Network Adapter
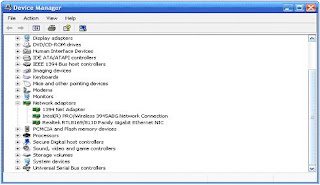
Figure 1. Checks the existence of the wireless ethernet
 Figure 2. Display the application wireless ethernet
Figure 2. Display the application wireless ethernet4. On the tab, there are several configuration settings such as network administration looks at the picture 3 |
 Figure 3. Network administration configuration settings
Figure 3. Network administration configuration settingsa. Select profile: optional default or user provided certain Access Point.
Example: Select Profile: network.
b. Service Set Identifier (SSID): the name of the road (networkID) as well as on the wired LAN which is a front guard for wireless data security system. To be able to access the access points into the center of the wireless network system, workstation must know the SSID used by the nearest access point. SSID can be easily user set in the settings for "broadcast"
Example: SSID: marionette kites
c. Channel: the channel frequency used by wireless ethernet is the difference between the frequency of each channel 5 MHz channels with the number of which varies depending on the manufacturer of tools
Example: Channel: 11
d. Encryption: encryption mode for the data to be transferred, if the consequences of this mode is activated the traffic network to be slow
e. Operating Mode:
802.11 Adhoc configuration for point-to-point networking
Insfrastructure configuration for multi-point networking
5. Link Information tab on the image such as 4, there are two bars and the quality of the network signal strength
6. Tab IP information
7. Site Survey Tab: used to scan the existence of the access point, is more than one wireless network is detected as in the picture 6
2. Setting up wireless dynamic, as follows:
After knowing the steps / how it works, then praktikan akan menganalisanya based on the results of the data is as follows:
ü Network WLAN is easy to implement, very neat in the case of physical information that can proceed without any seutas cable, very flexible because it can be implemented in almost all locations and at any time, and that is not bound to use it in one place only. With all the factors that have this, its users can do the work of more easily result into a job done more quickly, does not require a long time only because of physical problems from the network PC that they use. Based on this factor, the wireless LAN can not directly increase the productivity of the work of its users. Quite a lot of factors that exist in the resistor network cable can be removed if you are using this medium. Increasing the productivity of employees, will be very useful for companies where they work, is not it?
ü In the development of wireless networks there are two types of model or network that is point to point (ad hoc) model and multi-point (infrastructure). Point to point means that only one client computer connected to one another kmputer (one configured as a transmitter and one configured as a receiver, so the network is only the second form on the computer before (missed communication data directly without passing through access point). Multi-point (infrastructure) means that all computers will be connected to the access point will sehinngga network from all computers that are on the wilyah coverage access point earlier, data communication is done through the Access point. This network topology as star.
ü Wireless Network is superior in problems where the network cable from the wireless network using the media as intermediaries in the waves elektomagnetik raised from the transmitter (access point on the model or multi-point wireless ethernet transmitter pad of the computer models point to point). elektromagnetik this wave emission has a certain range depending gelombangnya strong, the network will reach this area in the position where the client is located. So the wireless network is very flexible to the place.
ü Data on the wireless network is transmitted through the wave elektromagnetik that is the way the data will be sent to the computer with the sender dimodulasi wave elektromagnetik (together) and then the data with electro magnetic waves sent to the client computer or dituju, and then on the recipient's computer data is separated from electro magnetic waves (demodulasi) so that data can be read.
ü One of the business in the security of data is as follows:
§ Using encryption
§ Using a strong encryption
§ Using the default password administratror
§ off the SSID broadcasting
§ off the WAP when not in use
§ Change the default SSID
§ Use MAC filtering
§ isolate the network from wireless LAN
§ Controlling the wireless signal
§ emit waves at different frequensi
F. CONCLUSION
Þ Wireless Network can be built in two forms, namely point-to-point (ad hoc) and multipoint (infrastructure).
Þ To build wireless networks in the form of a Local Area Network (LAN), only need to have a transmitter and the receiving device to build a wireless network. Once in possession, a little configuration and is ready for use kemudan a new data communications network in the desired location.
Þ One of the business in the security of data is as follows:
§ Using encryption
§ Using a strong encryption
§ Using the default password administratror
§ off the SSID broadcasting
§ off the WAP when not in use
§ Change the default SSID
§ Use MAC filtering
§ isolate the network from wireless LAN
§ Controlling the wireless signal
§ emit waves at different frequensi
SMCWUS
 BT-G2
BT-G2- Model: SMCWUSBT-G2
- Size: 17.01 Mb
- Version: 2.0.0.1
- Date added: 16-Oct-2007, 06:50
- Manufacturer: SMC
- Device type: Network
- Operation system: Win98 / WinME / WinXP / Windows2000 / Windows2003 / Windows Vista Home Basic
- MD5: a919d3751d57481cfad7afbd0ad06f3a










No comments:
Post a Comment